Organizations investing heavily in cybersecurity training programs face a persistent challenge: maintaining trainee motivation, accelerating skill development, and retaining newly trained security professionals in competitive markets where qualified talent commands premium compensation. Traditional training approaches focus almost exclusively on technical curriculum while overlooking the powerful motivational impact of strategic recognition programs that celebrate achievement, validate progress, and build professional identity within security teams.
Cybersecurity trainee recognition programs transform training investments from transactional skill transfers into meaningful professional development experiences that strengthen organizational culture, accelerate learning outcomes, and dramatically improve retention of security talent. By systematically acknowledging training milestones, certification achievements, project contributions, and skill demonstrations, organizations create environments where trainees feel genuinely valued while building careers rather than merely completing coursework.
Security leaders implementing comprehensive recognition programs through solutions like Rocket Alumni Solutions report measurable improvements in training completion rates, accelerated time-to-productivity for new security staff, enhanced team cohesion, and significantly improved retention of cybersecurity professionals who otherwise might quickly transition to external opportunities offering higher compensation but less supportive development environments.
Why Cybersecurity Trainee Recognition Matters
The cybersecurity talent shortage creates intense competition for skilled professionals, with organizations struggling to fill critical security positions while facing rapidly evolving threat landscapes. Training programs represent substantial organizational investments—typically requiring 6-18 months to develop entry-level personnel into productive security analysts, engineers, or administrators. Recognition programs maximize these investments by accelerating skill development through positive reinforcement, strengthening organizational commitment that improves retention, and building security team cultures that attract additional talent through reputation and referrals. Digital recognition displays provide visible proof that security organizations genuinely value professional development, creating competitive advantages in talent markets where skilled practitioners evaluate opportunities based on growth potential alongside compensation.
The Unique Challenges of Cybersecurity Training Programs
Cybersecurity training presents distinctive challenges that recognition programs can effectively address when designed with understanding of security workforce development dynamics.
Steep Learning Curves and Technical Complexity
Security disciplines require mastery of complex technical domains spanning network architecture, operating systems, programming languages, security tools, threat intelligence, incident response procedures, compliance frameworks, and risk management methodologies. Trainees often feel overwhelmed by the breadth and depth of knowledge required for competency, leading to discouragement that undermines motivation and increases attrition.
Recognition programs combat this challenge by breaking overwhelming journeys into achievable milestones worth celebrating. Rather than waiting until trainees achieve full competency—potentially 12-18 months into training—organizations can recognize foundational achievements like completing specific course modules, passing certification exams, successfully handling first incidents independently, contributing to security documentation, or presenting threat briefings to teams.

This milestone-based recognition transforms daunting long-term skill development into series of achievable near-term goals that maintain motivation through sustained positive reinforcement. Each recognition event validates progress while building confidence that full competency remains attainable through continued effort.
High Pressure and Stress in Security Roles
Cybersecurity professionals operate in high-stress environments where mistakes carry serious consequences—data breaches, system compromises, regulatory violations, or business disruptions. Trainees entering these roles often experience imposter syndrome, questioning whether they possess adequate skills for responsibilities they shoulder. This stress intensifies during incidents when trainees must make rapid decisions affecting organizational security posture.
Strategic recognition addresses stress by providing regular validation that trainees are developing appropriate skills and making valuable contributions. Public acknowledgment of successful incident handling, effective troubleshooting, or valuable security improvements reinforces that trainees are genuinely becoming competent professionals rather than perpetually struggling beginners. This validation reduces anxiety while building professional confidence essential for effective security work.
Organizations should explore approaches to employee recognition through touchscreen displays that demonstrate systematic commitment to acknowledging security team contributions across all experience levels.
Retention Challenges in Competitive Markets
Cybersecurity talent shortage creates exceptionally competitive job markets where skilled practitioners receive constant recruiting approaches offering substantial compensation increases. Organizations investing in trainee development frequently lose newly competent staff to external opportunities once training investments bear fruit, forcing continuous replacement cycles that waste resources while degrading institutional security knowledge.

Recognition programs improve retention by creating emotional connections to organizations and teams that transcend purely financial compensation considerations. When trainees see their achievements celebrated publicly, their names and accomplishments displayed prominently, and their contributions to organizational security acknowledged systematically, they develop stronger organizational loyalty and professional identity tied to specific security teams. These connections create retention advantages that help organizations compete for talent against higher-paying competitors lacking comparable development cultures.
Research on recognition solutions and their impact demonstrates measurable retention improvements when organizations implement comprehensive acknowledgment programs that make employees feel genuinely valued beyond compensation alone.
Core Components of Effective Cybersecurity Recognition Programs
Trainee recognition systems require thoughtful design incorporating elements specifically relevant to security workforce development rather than generic employee appreciation approaches.
Certification and Credential Achievement Recognition
Industry certifications represent major training milestones demonstrating validated competency across security domains. Common certifications deserving recognition include foundational credentials like CompTIA Security+, Network+, and CySA+, advanced certifications such as CISSP, CISM, CEH, and OSCP, specialized credentials covering cloud security, penetration testing, or incident response, and vendor-specific certifications for security tools and platforms organizations deploy.
Certification achievement recognition should include public announcement through team communications and digital displays, professional photography capturing celebratory moments, detailed profiles highlighting certification significance and skills demonstrated, addition to organizational certification boards tracking team credentials, and financial rewards or bonuses when budget permits complementing public acknowledgment.
Recognition Elements for Certifications
- Certification Profile: Detailed description of certification requirements, skills validated, and industry recognition level
- Personal Achievement Story: Trainee reflection on preparation journey, challenges overcome, and professional growth
- Study Investment: Documentation of hours invested, resources utilized, and preparation approach
- Career Milestone Context: How certification advances trainee career goals and team capabilities
- Congratulations Messages: Recognition from leadership, mentors, and colleagues celebrating achievement
- Future Goals: Next certification targets or skill development objectives
Display and Visibility Options
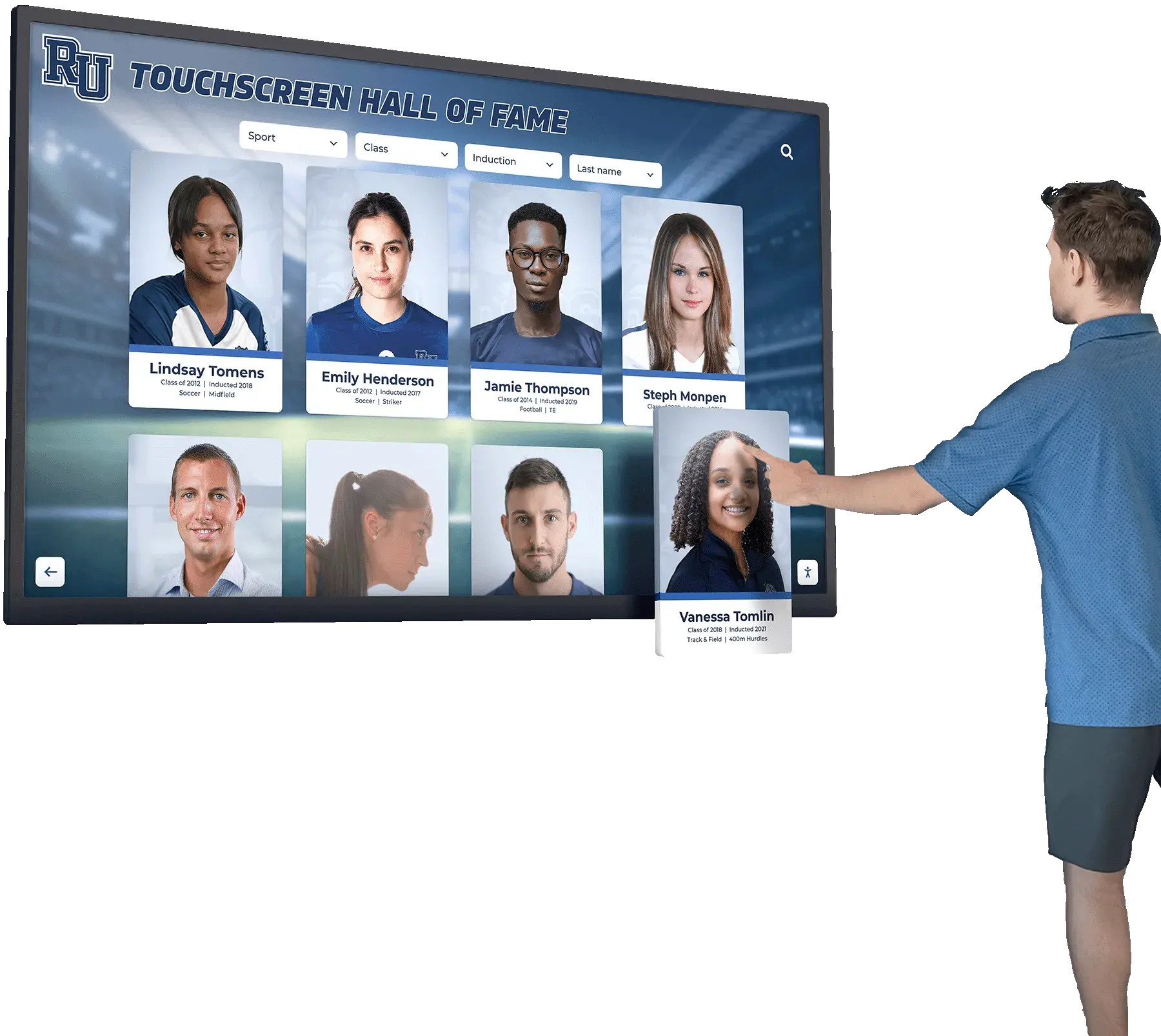
- Digital Recognition Displays: Interactive touchscreens in security operation centers or common areas showcasing certifications
- Team Certification Boards: Visual displays tracking all team member credentials and specializations
- Internal Communications: Announcements through email, Slack channels, or team meetings
- Social Media Recognition: Public celebration on company LinkedIn or Twitter accounts (with permission)
- Executive Acknowledgment: Recognition from senior security leadership or organizational executives
- Website Features: Profiles on internal or external websites highlighting team expertise
Organizations implementing certification recognition should review guidance on digital trophy displays that showcase professional achievements without physical space limitations inherent in traditional approaches.
Hands-On Training Milestone Recognition
Beyond formal certifications, hands-on training programs include numerous milestones worth celebrating as trainees develop practical security skills through labs, simulations, capture-the-flag competitions, red team exercises, and real-world projects.
Training milestone recognition might celebrate achievements such as completing specific training modules or course sequences, successfully exploiting vulnerabilities in penetration testing labs, solving complex security challenges in CTF competitions, building functional security tools or automation scripts, completing security architecture design projects, or contributing to team knowledge bases with technical documentation.
These hands-on achievements often demonstrate practical competency more effectively than written exams, making them particularly valuable recognition opportunities that reinforce skill application over theoretical knowledge.
Incident Response and Real-World Contribution Recognition
Perhaps most valuable recognition acknowledges trainee contributions during actual security incidents, investigations, or operational activities where their developing skills generate tangible value for organizations and teams.
Real-world contribution recognition might highlight achievements like independently handling first security alerts or incidents, identifying previously undetected threats or vulnerabilities, contributing valuable insights during incident investigations, successfully implementing security controls or monitoring improvements, or developing automation that improves security operations efficiency.
This recognition proves especially powerful because it validates that trainees are becoming genuine security professionals contributing meaningful value rather than students consuming training resources. Public acknowledgment of real operational contributions accelerates professional identity development while demonstrating to teams that trainees are transitioning into full security team members.
Resources on staff recognition in organizational settings provide frameworks applicable to security teams seeking to celebrate diverse contribution types beyond traditional achievement categories.
Peer Recognition and Team Acknowledgment
While leadership recognition carries weight, peer acknowledgment from experienced security professionals holds special significance for trainees developing professional identities and seeking acceptance within security communities.

Peer recognition programs enable security team members to nominate trainees for acknowledgment based on observed achievements, helpful collaboration, valuable contributions, or professional growth. These programs might include monthly peer recognition awards, team-voted acknowledgments during retrospectives, kudos systems integrated into collaboration platforms, or mentor nominations highlighting trainee progress.
Peer recognition proves particularly effective because it demonstrates that trainees have earned respect from security practitioners whose professional judgment they value highly. This acceptance within security communities accelerates professional identity formation while building team cohesion across experience levels.
Implementing Cybersecurity Trainee Recognition Programs
Successful recognition program implementation requires systematic planning addressing security team culture, training program structure, and organizational dynamics unique to security operations.
Assessment and Program Design
Begin by evaluating current training programs and recognition gaps through activities such as surveying trainees about recognition preferences and motivational factors, interviewing security leadership about retention challenges and cultural goals, reviewing training curricula identifying natural milestone opportunities, examining existing recognition approaches determining what works and what falls short, and researching best practices from high-performing security teams and training programs.
This assessment informs recognition program design decisions about which achievements merit recognition, how recognition will be delivered and publicized, what resources are required for sustainable operations, and how effectiveness will be measured and optimized over time.
Integration with Training Curriculum
Recognition programs achieve maximum impact when tightly integrated into training curriculum rather than treated as separate initiatives. This integration includes defining clear achievement milestones throughout training progressions, establishing recognition criteria for each milestone based on demonstrated skills, scheduling recognition events aligned with training phases and cohort graduations, creating recognition content templates streamlining acknowledgment processes, and connecting recognition to career development paths and promotion criteria.
Organizations should explore approaches to digital recognition that support training programs by providing systematic platforms for acknowledging diverse achievement types across extended training timelines.
Technology Platform Selection
Digital recognition platforms provide practical infrastructure for sustainable programs reaching distributed security teams while maintaining comprehensive achievement archives. Important platform capabilities include user-friendly content management enabling easy profile creation and updates, multimedia support for photos, videos, and achievement documentation, searchable databases allowing trainees and visitors to explore accomplishments, integration with HR systems, learning management platforms, or badge systems, analytics tracking engagement and demonstrating program impact, and mobile accessibility ensuring recognition reaches remote security team members.
Solutions like Rocket Alumni Solutions offer specialized platforms designed for recognition programs requiring extensive customization, integration capabilities, and ongoing support that security organizations need for successful long-term operations.

Cultural Change Management
Recognition programs represent cultural interventions requiring change management ensuring organizational support and participation. Effective approaches include executive sponsorship from Chief Information Security Officers or security leadership, communication campaigns explaining program purposes and participation processes, leadership modeling through consistent recognition from managers and senior security staff, feedback mechanisms gathering trainee and staff input for continuous improvement, and patience recognizing that cultural adoption requires sustained effort over quarters or years.
Organizations underestimating cultural aspects often implement technically sound recognition systems that achieve minimal engagement because security teams don’t understand value, leadership doesn’t participate consistently, or recognition feels forced rather than authentic. The resources on white-glove support and customer success highlight how ongoing guidance helps organizations navigate cultural challenges during recognition program adoption.
Measuring Recognition Program Impact
Effective recognition programs require systematic measurement demonstrating value while identifying improvement opportunities that optimize training outcomes and retention results.
Training Performance Metrics
Quantitative training metrics document whether recognition influences learning effectiveness and skill development including training completion rates for courses, certifications, and program phases, time-to-competency measuring duration from training start to independent operational capability, assessment scores on technical exams, practical exercises, and skill evaluations, certification pass rates on first attempts versus industry averages, and skill retention measured through follow-up assessments weeks or months after training completion.
Comparing these metrics before and after recognition program implementation reveals whether acknowledgment influences learning outcomes beyond traditional curriculum and instruction alone. Organizations frequently discover that recognition improves completion rates while reducing time-to-competency by maintaining trainee motivation through challenging skill development periods.
Retention and Career Development Metrics
Recognition programs ultimately aim to improve security workforce retention and career development including voluntary turnover rates for security staff particularly within first 2-3 years, time-in-position before promotion to advanced security roles, internal mobility with trainees advancing into specialized security functions, recruiting effectiveness measured through candidate quality and acceptance rates, and employee satisfaction scores specifically for professional development and recognition items.
Recognition Program Impact on Security Workforce Metrics
| Workforce Metric | Typical Impact Range | Contributing Factors | Measurement Approaches |
|---|---|---|---|
| Trainee Retention | 20-35% improvement | Stronger organizational connection, career development satisfaction, team culture | Turnover rates, exit interview feedback, tenure analysis |
| Training Completion | 15-25% increase | Enhanced motivation, milestone clarity, positive reinforcement | Completion rates, drop-out analysis, time-to-completion |
| Certification Success | 10-20% improvement | Recognition motivation, study investment, peer support | Pass rates, first-attempt success, certification velocity |
| Time to Productivity | 15-30% reduction | Accelerated skill development, confidence building, clear progression | Manager assessments, operational metrics, independence timelines |
| Team Culture Health | Significant positive shift | Recognition culture, peer relationships, organizational pride | Engagement surveys, culture assessments, team cohesion indicators |
Recognition impact on retention proves especially valuable given cybersecurity workforce economics. When recognition programs improve trainee retention by even 20%, organizations save substantial costs from reduced recruiting, onboarding, and training investments while maintaining institutional security knowledge that departing staff would otherwise take to competitors.
Engagement and Program Utilization Metrics
Recognition platform analytics reveal whether programs achieve intended visibility and engagement including display interaction frequency measuring touchscreen usage in security operations centers, profile view analytics showing which achievements receive attention, search query patterns revealing what trainees and visitors seek, recognition content additions tracking ongoing program activity, and social sharing measuring external amplification through professional networks.
Low engagement metrics signal problems requiring attention—perhaps recognition content lacks compelling detail, displays suffer poor placement or visibility, or communication about programs remains insufficient for awareness building.
Specialized Recognition Approaches for Security Training
Cybersecurity training programs benefit from recognition approaches specifically designed for security workforce development contexts rather than generic employee appreciation programs.
Capture the Flag and Competition Recognition
Security training increasingly incorporates gamified learning through capture-the-flag competitions, security challenges, and simulated attack-defense exercises. These competitions provide natural recognition opportunities celebrating top performers, innovative approaches, and notable achievements.

CTF recognition might include leaderboards showcasing competition standings, challenge solution spotlights highlighting creative approaches, speedrun recognition for fastest challenge completions, write-up features sharing detailed solution documentation, and year-end awards celebrating consistent competition performance across events.
Public recognition of competition achievements motivates continued participation while building friendly competitive dynamics that accelerate skill development through peer learning and challenge.
Red Team and Penetration Testing Achievements
Advanced security training often includes red team exercises where trainees practice offensive security techniques against controlled targets. Successful exploitation, privilege escalation, persistence establishment, or defense evasion deserve recognition as significant skill demonstrations.
Recognition for offensive security achievements requires careful sensitivity to organizational security—public details about successful attacks might expose vulnerability information inappropriate for broad visibility. Recognition can acknowledge achievement significance without revealing sensitive technical details that should remain restricted to security teams.
Security Tool Development and Automation
Trainees who develop security tools, automation scripts, or operational improvements contribute lasting value extending beyond their individual skill development. Recognition for tool development might feature achievements like custom security scripts improving operational efficiency, integration projects connecting security platforms, dashboards providing visibility into security metrics, documentation resources supporting team knowledge sharing, or open source contributions to security community projects.
These contributions demonstrate initiative and creativity while building practical software development skills increasingly important for modern security practitioners. Recognition reinforces that security work extends beyond monitoring alerts to include creative problem-solving and operational innovation.
Resources on creating digital walls of achievement provide frameworks for showcasing diverse accomplishment types including technical projects and operational contributions unique to security team environments.
Mentorship and Knowledge Sharing Recognition
Security training benefits substantially from experienced practitioners mentoring trainees and sharing operational knowledge. Recognition programs should celebrate mentorship contributions including senior staff dedicating time to trainee development, subject matter experts delivering technical training or workshops, incident responders guiding trainees through investigations, and technical writers contributing to security knowledge bases and documentation.
Recognizing mentorship validates that knowledge sharing represents valued contribution rather than distraction from “real work,” encouraging continued investment in trainee development that accelerates team capability growth.
Building Security Team Culture Through Recognition
Recognition programs contribute to security team culture development beyond individual trainee motivation, strengthening organizational dynamics that improve overall security operations effectiveness.
Creating Security Professional Identity
Trainees entering cybersecurity often lack clear professional identity, viewing themselves as students learning rather than security practitioners contributing. Recognition accelerates professional identity formation by publicly acknowledging trainees as valued security team members whose contributions strengthen organizational security posture.
This identity shift proves psychologically important—professionals typically invest more effort, take greater ownership, and demonstrate stronger commitment than students merely completing coursework. Recognition programs accelerate this psychological transition by treating trainees as emerging professionals deserving acknowledgment rather than subordinates consuming resources.
Fostering Collaborative Learning Cultures
Security teams perform best when members collaborate freely, share knowledge openly, and support collective skill development. Recognition programs reinforce collaborative values by celebrating teamwork, knowledge sharing, mentorship, and mutual support alongside individual technical achievements.
Organizations should balance individual achievement recognition with team accomplishment acknowledgment ensuring recognition systems don’t inadvertently create competitive dynamics undermining collaboration essential for effective security operations.
Building Organizational Security Pride
Public recognition of training achievements builds organizational pride in security team capabilities and professional development cultures. When organizations prominently display security team certifications, achievements, and contributions through solutions like interactive touchscreen displays in lobbies or operation centers, they demonstrate visible commitment to security excellence that strengthens recruiting, improves executive awareness of security capabilities, and builds organizational confidence in security team competency.
This visibility proves especially valuable in organizations where security teams historically operated invisibly unless breaches occurred—positive recognition reshapes organizational narratives about security from cost center to capability differentiator.
Addressing Recognition Program Challenges
Organizations implementing cybersecurity trainee recognition frequently encounter obstacles requiring thoughtful navigation for successful outcomes.
Maintaining Recognition Authenticity and Standards
Recognition programs lose credibility when applied inconsistently or granted for insufficient achievements. Organizations must establish clear criteria defining recognition-worthy accomplishments while communicating standards transparently to maintain program integrity.
Overly generous recognition—acknowledging minimal achievements or routinely expected performance—devalues genuine accomplishments while creating cynicism about program authenticity. Conversely, excessively stringent standards that make recognition virtually unattainable fail to motivate trainees who perceive acknowledgment as unrealistic regardless of effort invested.
Balancing Public Recognition with Individual Preferences
While public recognition motivates many trainees, some individuals prefer private acknowledgment feeling uncomfortable with public attention or visibility. Effective programs accommodate diverse preferences through tiered recognition approaches offering public celebration for those who desire it alongside private acknowledgment respecting those preferring lower-profile appreciation.

Organizations should explicitly ask trainees about recognition preferences rather than assuming everyone values identical acknowledgment approaches, building flexibility into recognition systems that honor individual comfort levels while maintaining program effectiveness.
Sustaining Recognition Programs Long-Term
Initial enthusiasm for new recognition programs often fades without systems ensuring sustained operations. Long-term sustainability requires clear role assignment defining recognition program responsibilities, realistic time allocation acknowledging work required for content creation and management, budget commitment supporting platform costs and recognition events, executive support maintaining priority during competing demands, and process documentation enabling continuity through personnel transitions.
Recognition programs that depend entirely on individual champions frequently collapse when those individuals transition to other roles, making organizational embedding essential for programs intended to strengthen culture over years and decades.
Future of Cybersecurity Training Recognition
Recognition technology and practices continue evolving, bringing new capabilities enhancing effectiveness for security workforce development applications.
Digital Badges and Credential Verification
Blockchain-based digital badges and verifiable credentials increasingly supplement traditional certifications, providing tamper-proof achievement records that trainees can share across professional networks. Recognition programs integrating digital badge ecosystems enable achievement portability while providing cryptographic verification of skills and accomplishments.
AI-Powered Personalized Recognition
Artificial intelligence systems can analyze training progress, identify recognition-worthy achievements, and suggest appropriate acknowledgment timing and formats based on individual trainee profiles and preferences. These intelligent systems ensure consistent recognition across security teams while reducing administrative burden on managers and training coordinators.
Virtual and Augmented Reality Recognition Experiences
Emerging VR and AR technologies enable immersive recognition experiences where trainees participate in virtual award ceremonies, explore 3D achievement galleries, or visualize skill development progressions through interactive data representations that transcend traditional two-dimensional display limitations.
Integration with Career Development Platforms
Modern recognition systems increasingly integrate with career development platforms connecting training achievements to career progression opportunities, compensation decisions, and professional development planning. This integration ensures recognition influences tangible career outcomes beyond symbolic acknowledgment alone.
Building Stronger Security Teams Through Recognition
Cybersecurity trainee recognition programs represent strategic investments in security workforce development that generate measurable returns through improved retention, accelerated skill development, and strengthened team cultures supporting operational excellence.
Organizations serious about cybersecurity workforce challenges recognize that recruitment and training alone prove insufficient without retention strategies addressing competitive talent markets where newly trained security professionals receive constant external opportunities. Recognition programs create emotional connections and professional identity formation that improve retention substantially beyond compensation-only approaches.
Effective recognition requires systematic design incorporating certification achievements, hands-on training milestones, real-world contributions, and peer acknowledgment through platforms providing sustained visibility and accessibility. Implementation demands attention to security team culture, change management, technology infrastructure, and measurement systems demonstrating value while enabling continuous optimization.
Budget and resource constraints need not prevent meaningful recognition—even modest programs acknowledging achievements through team communications, public displays, and leadership attention generate positive impacts when implemented authentically and sustained consistently over time.
In security disciplines facing perpetual talent shortages and rapidly evolving threats, organizations that invest in training while systematically recognizing achievement build competitive advantages through superior retention, accelerated capability development, and stronger team cultures that attract additional talent through reputation and referral.
For security organizations ready to transform training investments into sustained workforce advantages, solutions like Rocket Alumni Solutions provide comprehensive platforms combining recognition technology with flexible content strategies supporting diverse security training contexts. Additional guidance on recognition approaches appears in resources covering employee recognition displays, achievement showcase strategies, and organizational recognition impact that strengthen professional development cultures across industries including cybersecurity.
When security trainees see their achievements celebrated visibly and permanently, they develop stronger organizational commitment, accelerated professional identity, and lasting connections to security teams and missions that transcend purely transactional employment relationships—creating workforce stability that transforms training investments from costs into enduring competitive advantages in perpetually challenging cybersecurity talent markets.